What is TPM?
Trusted Platform Module is a technology designed to provide hardware and software security-related functions. TPM identifies both the international standard to create a chip for cybersecurity and the chip itself. Trusted Computing Group (TCG) is the organization that publishes and maintains TPM specification through international standard 11889 ISO/IEC.
TPM helps with actions such as generating, storing and limiting the use of cryptographic keys, password end certificates.
History:
2009: Creation of standard TPM Main Specification Version 1.2 as ISO/IEC 11889:2009
2011: Release of final TPM Main Specification Version 1.2
2014: Announce of TPM Library Specification 2.0, first major update
2019: Release of edition 2.0, version ISO/IEC 11889:201
Cryptographic keys

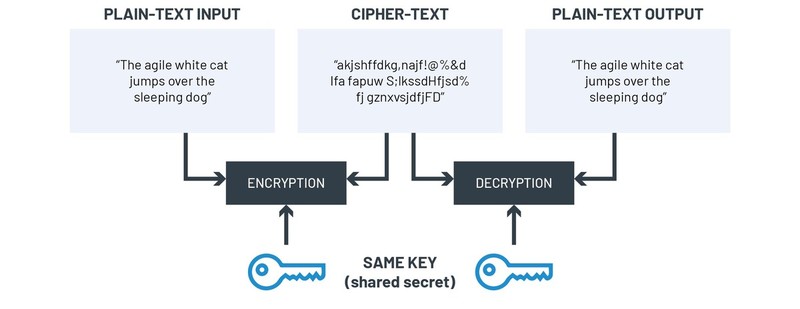
When you need to secure something, the cryptographic software or algorithm takes the original data and combines it with a long random string to create a new secure encrypted data.
The random string is called cryptographic key.
Only a user that has the cryptographic key can decrypt the data and read the original value.
Do I need a TPM?


• TPM is a technology for securing endpoints (*)
• IEC 62443-4-2 mentions TPM as the gold standard to meet the requirements of SL3 and SL4
• Verifies that the operating system and the device’s firmware are not manipulated
• Store digital credentials in a hardware-based vault
• Set password and manage keys
• Augment smart cards, fingerprint readers and fobs for multi-factor authentication
• Encrypt files and folders to control access
• Establish state information to enable endpoint integrity
• Enable more secure VPN, remote and wireless access
• For Windows® 11, TPM 2.0 is a requirement (PC Must have TPM Enabled)
(*) Industrial Internet Security Framework (https://www.iiconsortium.org/IISF.htm)
Discrete module and integrated TPM


Discrete Trusted Platform Module (dTPM) is a dedicated microcontroller designed to secure hardware. It integrates cryptographic keys into devices and is used for secured crypto processes as well as for secured storage of critical data.
In recent years, the integrated TPM in x86 based machines has been introduced. In this form, TPM is implemented inside (integrated) an existing platform component chipset. For example, x86 based integrated TPM functionality is a module of the security and management engine, and it is logically isolated from the other modules of the engine.
When following the specification by the Trusted Computing Group, these implementations accomplish the same functions of TPM.
iTPM vs dTPM
Asem products TPM
Considerations


• The user should make the appropriate considerations based on the application, perceived security risks and understanding of the variants of TPM
• Both iTPM and dTPM can be TCG TPM 2.0 ISO/IEC 11889:2015 compliant
• Some smaller systems do not have the additional space for a dedicated module
• Discrete module TPM implementations have a higher cost on the system
Personal area
Login to your personal area to download your restricted contents. If you don’t have am ASEM account yet, register here.